Recent Posts
Archives
Categories
CyberDefenders | PoisonedCredentials | Incident Investigation in Network Security

Scenario:
The security team of your organization has recently identified a surge in suspicious network activity, raising concerns about potential LLMNR (Link-Local Multicast Name Resolution) and NBT-NS (NetBIOS Name Service) poisoning attacks within the network. These attacks exploit protocols to intercept network traffic and compromise user credentials. Your responsibility is to delve into network logs and analyze captured traffic using Wireshark.
Tools:
-
- Wireshark
Question 1: Identifying the Mistyped Query
In the context of the incident, the attacker initiated actions by leveraging benign network traffic from legitimate machines. By filtering LLMNR Protocol and the IP address 192.168.232.162, a mistyped query was identified. The specific query was (fileshaare), with the correct query being (fileshare).

Answer: fileshaare
Question 2: Determining the Rogue Machine’s IP Address
For a thorough investigation, it’s essential to determine the IP address of the rogue machine. By examining packets 55 or 56, the rogue machine’s IP address was identified as 192.168.232.215.

Answer: 192.168.232.215
Question 3: Identifying the Victim Machine
In the investigation, identifying all affected machines is crucial. The IP address of the second machine receiving poisoned responses from the rogue machine was determined by filtering the PCAP with the attacker’s IP address (192.168.232.215). The victim’s IP address is 192.168.232.176.
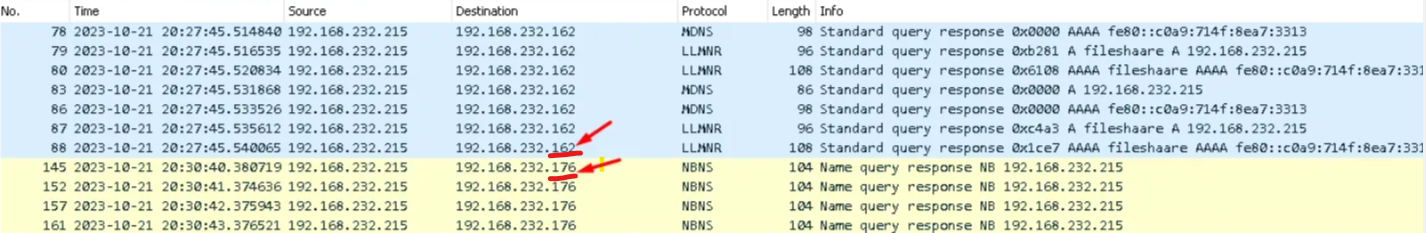
Answer: 192.168.232.176
Question 4: Username Associated with Compromised Account
To assess potential compromised accounts, filtering the PCAP with the attacker’s IP and SMP2 Protocol was performed. The username associated with the compromised account is “janesmith.”

Answer: janesmith
Question 5: Hostname of the Accessed Machine via SMB
To understand the extent of the attacker’s activities, examining packet 242 and following TCP stream revealed that the hostname of the victim machine accessed via SMB is “AccountingPC.”

Answer: AccountingPC
