All posts by MrGuato
Updating Your Valheim Server

I am writing this article as I had some issues figuring out how to update Valheim Server and its correct path using steamcmd. This goes into step by step on how it’s done so you can return to slaying trolls! Step 1: We need to log in to your Linux Server and go to the…
CyberDefenders | PoisonedCredentials | Incident Investigation in Network Security

In the unfolding narrative of network security, the organization’s vigilant response to a surge in suspicious activity reveals a clandestine web of LLMNR and NBT-NS poisoning attacks. Armed with tools like Wireshark, the investigation meticulously traces the attacker’s footsteps. A mistyped query, “fileshaare,” emerges from legitimate network traffic, providing a subtle entry point. Through the digital fog, the rogue machine’s IP address is exposed at 192.168.232.215, while a second victim’s IP, 192.168.232.176, bears witness to the extent of the intrusion. Compromised user credentials lead to the unmasking of “janesmith” as the targeted account, and the accessed machine’s hostname, “AccountingPC,” offers a glimpse into the attacker’s activities. This cybersecurity odyssey underscores the imperative of swift detection and response in safeguarding the network’s resilience.
Stay Safe Online: Your One-Stop Shop for Free Cybersecurity Tools

In today’s digital age, cybersecurity is more important than ever. But for small businesses, it can be tough to know where to start. That’s where Stay Safe Online comes in.
Empowering Cybersecurity: A Deep Dive into PolySwarm and Its Free Tools for Your Cyber Toolbox
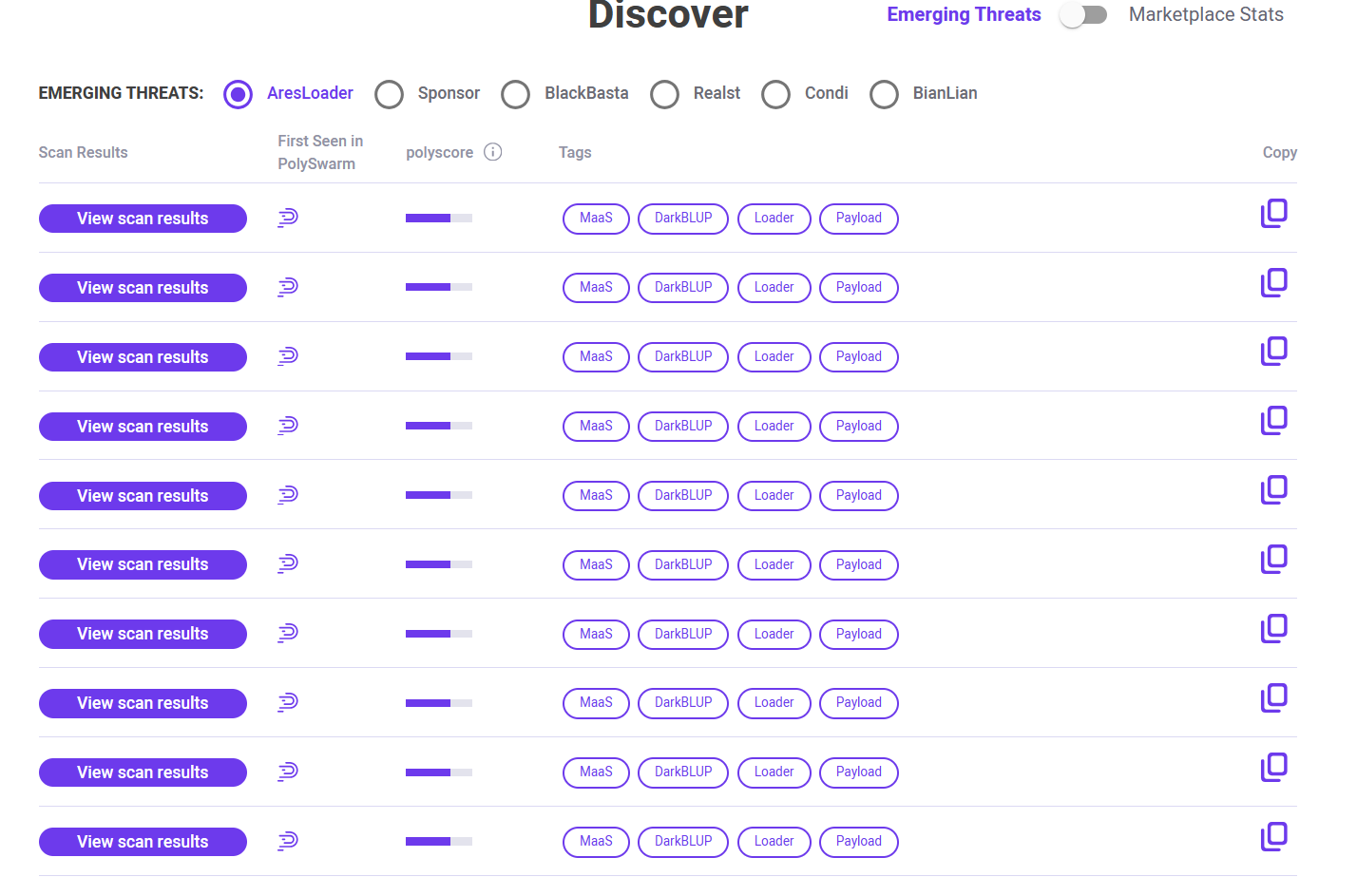
PolySwarm revolutionizes cybersecurity by embracing a decentralized approach to threat intelligence. Its collaborative ecosystem, fueled by a global community of experts, creates a dynamic defense against evolving cyber threats. In a world where innovation is the key to security, PolySwarm stands as a beacon of effective and adaptive cybersecurity solutions.
